All About Risk Management Enterprise
Risk Management Enterprise for Beginners
Table of ContentsSome Known Details About Risk Management Enterprise Risk Management Enterprise Fundamentals ExplainedThe Best Strategy To Use For Risk Management Enterprise
Control who can watch or modify these components by establishing certain gain access to rights for specific customers, making sure details protection and customized usability. Permits customers to customize their user interface by choosing and setting up important information aspects. Offers a personalized experience by permitting modification of where and just how data components are presented.It permits accessibility to real-time incorporated data immediately. Facilities can use thorough data intelligence for quicker and much more informed decision-making.
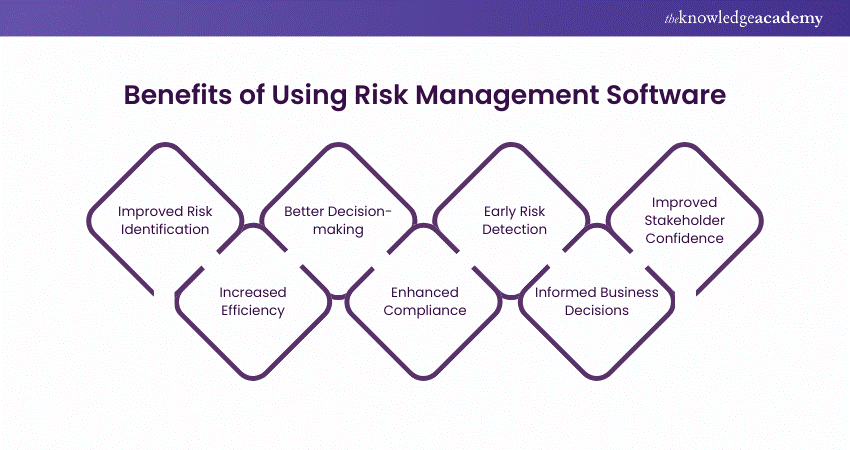

Diligent is a risk administration software application that permits optimizing performance, and enhances growth. It likewise assists keep an eye on threats with ERM software that includes integrated analytics and adapts to your company demands.
Little Known Facts About Risk Management Enterprise.
Simplifies the process of collecting threat information from numerous parts of the organization. Supplies leadership and the board with real-time danger understandings. Use ACL's sophisticated analytics to find threat patterns and forecast threats.
This permits companies to catch risk insights and red flags in the third-party vendor's safety and security record. Allows companies to record and document threat insights and red flags in third-party supplier safety records.
Recognizing dangers in development aids a facility get ready for audits. It also minimizes risk with structured compliance and threat management. As a result of this facilities won't have to juggle various systems for risk monitoring. The users of Hyperproof can streamline threat management in one location. It can aid collect and track all your risks in the Hyperproof danger register.
It provides fast accessibility to needed info and documentation. This guarantees the safety and security of Active proof go now circumstances by allowing multi-factor verification (MFA) utilizing authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
See This Report on Risk Management Enterprise
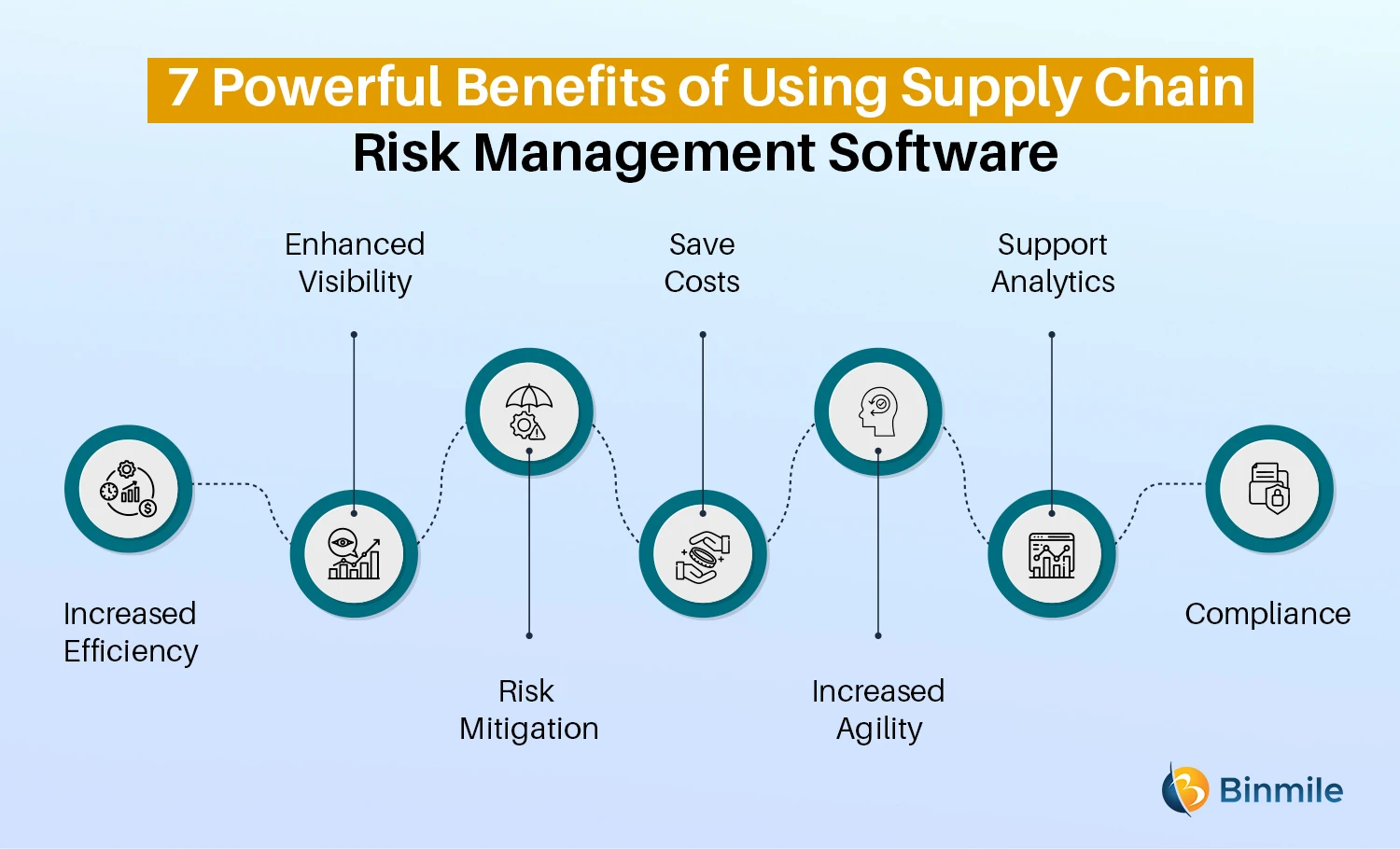
It makes it possible for smooth operations and combinations and decreases ineffectiveness. It gives top-tier safety and security features to safeguard sensitive data. This threat administration software program is an excellent tool for facilities wanting to deal with unneeded problems or risks. It features multiple sorts of features that make it particular for ERM supervisors. Right here we have highlighted several of its essential functions for your advantage, so have check my reference a look.
Individuals can additionally use the AI-powered devices and pre-existing content to produce, evaluate, prioritize, and address threats efficiently. Improves the procedure of setting up my sources and populating threat registers. Uses AI and collection web content to improve danger analysis precision. It allows faster recognition and reduction of risks, This is generally an aesthetic model.